Internet is a powerful thing, and today, with all the cloud-based applications, services, and all our business done mainly online – depending on your industry – and remotely, we are looking to leverage the amount of information we have access to. But we are also trying to protect our information even better.
We try to learn more about staying safe and protecting our data within the digital world in our need for constant knowledge. That’s where Cyber Security comes in.
And no, this is not something that came out of the matrix. Cyber Security is fundamental now more than ever to protect our digital assets and personal data integrity. At first, it can be daunting to learn about it. We think about hackers behind a screen and a complex virus that will shut down the world.
However, understanding the basics of cyber security is not that hard. Then, we can expand our knowledge and learn how to improve our online safety to identify common threats and ensure a healthy and secure environment.
Here are some basics to consider.
What is Cyber Security
In simple words, cyber security is the practice of defending computer systems, networks and data, against cyber-attacks or unauthorized access.
Nowadays, our daily life and activities rely on computers and the internet, such as emails, video games, social media, shopping and navigation systems. Because of this, there are many risks – some more serious than others – for example, viruses, malware, stealing credit card information and making unauthorized purchases.
Why do I need Cybersecurity while working remotely?
As the current situation around the world continues, remote work has become a necessity for many organizations. Unfortunately, this has also led to more cyber-attacks actively seeking to exploit weaknesses in the IT infrastructures.
Cyber security is needed while working remotely to protect the confidentiality of the company and its data and information. In addition, remote work gives the employees the ability to work from anywhere, and the employees can use public networks. They end up accessing their corporate accounts using unsecured wifi connections.
To help protect their employees and strengthen their knowledge, companies should create a guideline highlighting the types of cyber-attacks and how to prevent them.
How to prevent cyber-attacks and be safe while working remotely?
Here are some of the things corporate and remote workers must consider to stay safe online:
Strong Passwords
Pick a strong alphanumeric password with at least 12 characters that is entirely unrelated to your details, for example, no phone number, birthdates, names and addresses. In addition, always include at least one uppercase letter, a number and symbol (e.g., dollar sign, hashtag).
Below is a chart on how easy it is to crack a password based on its number of characters.
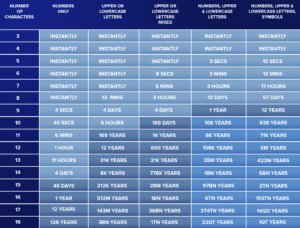
Don’t use the same password for multiple accounts because this could put you at high risk. For instance, imagine using one password for Facebook and some random shopping website. If the shopping website is hacked, and your credentials are leaked, the hacker can then try to use the leaked email and password on Facebook, and because you’re using the same password everywhere, the hacker will take over your Facebook account.
This is known as “credential stuffing”, where a hacker is able to use one leaked password to access all your other accounts
Secure Wifi
Hackers can potentially hack your wifi password and eavesdrop on these communications. When using the home wifi, the data sent over the wireless network should be encrypted. Encryption scrambles the transmitted data into a gibberish code so that it’s not readable by others. Using encryption is the most effective way to secure your network from intruders.
There are several types of available encryption in your router’s settings. The two main ones are wifi Protected Access (WPA) and Wired Equivalent Privacy (WEP).
WPA2 or WPA3 are the strongest and most secure ones and must be used when available. Note that many older routers use WEP encryption by default. WEP can be cracked in a matter of seconds.
Although WPA2 and WPA3 are the most secure encryption, a strong alphanumeric wifi password must be used with at least 12 characters long; otherwise, your wifi password will be prone to cracking.
When using public wifis, employees have no control over the security of their wifi internet connection, and anyone connected to the same wifi can steal your transmitted data (a process known as “sniffing”). That’s why it is advisable to use a VPN connection. This is necessary, especially when accessing websites or apps that transmit data over an unsecured network (for example, websites that start with HTTP instead of HTTPS).
If a VPN connection is not available, it’s best to avoid using the public wifi unless necessary. Even then, employees should make sure all the websites accessed are over SSL (starts with https://) and have a valid SSL certificate.
Phishing
Phishing is an attempt to trick you into giving out personal information such as email, password or a credit card number. Most of the time, phishing is done over emails, and the stolen data is then used to access important accounts and can result in identity theft and financial loss.
Phishing attacks are getting smarter every day and can bypass email spam filtering. Below is a list of things to do or avoid when checking your emails:
- Hyperlinks: Always hover a link before you click on it and look where you will be directed. This is because a hyperlink can have a different text than the actual link. For instance, if you click the following hyperlink facebook.com, it will redirect you to Gmail. A smarter, trickier way is to have a page that looks like a Facebook login page, and once the employee enters their email and password, their credentials will be stolen, and the page will redirect them to Facebook.
- Too Good To Be True: Whether you won a million dollars or an iPhone, an eye-catching offer is designed to attract people’s attention and trick them into sending personal information back to the sender.
- Use common sense: A favourite tactic is when you’re being told that your account will be suspended unless you update or reply with your details. The best approach is to never click on any link or reply to the email, instead visit the source website directly.
- Attachments: If you see an attachment in an email you weren’t expecting, or that doesn’t make sense, don’t open it!
Viruses, malware and ransomware
Viruses come in many forms, and they spread from one device to another using your internet connection or USB flash drives. They might damage your software or operating system, destroy your files, or even format your hard drive.
Contrary to popular belief, all operating systems such as Windows, macOS and Linux are subject to viruses. Anti-viruses are a great way to protect your system against viruses. Make sure your anti-virus definition files are up to date.
Similar to viruses, malware compromises your device and slows it down. They are usually responsible for stealing your data, controlling your device or using your computer resources for illegal activities such as attacking websites or even crypto mining.
Ransomware works slightly differently and is responsible for completely encrypting your files so you can’t open or access them. Once the files are encrypted, you’ll need a unique key or password to decrypt them, and the only way to retrieve this key is by paying a ransom to the attacker.
Ransomware is usually spread in spam email messages or pirated applications downloaded from the internet or torrents.
Updating your Operating system and Applications
Always keep your Operating system and applications up to date with the most recent security patches and upgrades. This will protect your systems from malicious attacks and fix any current bugs.
Cyber security may seem like something complicated to do. But the truth is that, with some basic knowledge, there are many things that we can do on our day-to-day to keep our data safe. With technology today, being user-friendly and easy to understand, there also comes new threats and issues we need to consider.
Don’t drop your guard. Be clever about cyber security. We can all set up a strategy to prevent any cyber-attacks and keep our information safe.




